3 min read
Building Culture That Works: Cobb Tech Named One of VA's Best
Cobb Technologies has been honored as one of the 2025 Best Places to Work in Virginia by Virginia Business and Best Companies Group. This prestigious...

It’s a topic we’ve touched on before in our “Why Legal Offices Must Make MFP Security A Top Priority” blog — but MFP security is a topic most definitely worth going into more detail about. Since 2018, TLS1.3 security has been available for client-server connections, and now MFPs are beginning to include this new, upgraded security protocol.
TLS stands for Transport Layer Security — it is a cryptographic protocol with the purpose of creating reliable, secure communications over or through a computer network. Some hallmarks of a TLS connection are:
So, what does all this mean exactly?
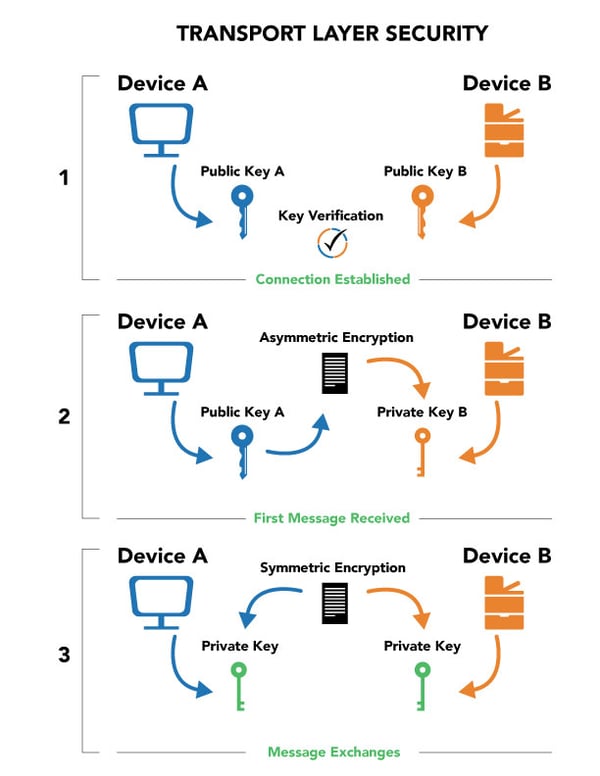
There are two forms of encryption that make TLS possible — asymmetric and symmetric. Think of it this way; an encrypted message requires a key to decipher it. Asymmetric encryption is used to describe when that key is different on both ends of the message — meaning the sender and receiver both have unique, separate keys used to decode the message. In the case of symmetric encryption, both the sender and receiver utilize the same key. Asymmetric encryption is slower, but more secure — symmetric is the opposite.
TLS uses both, and here’s why: creating a secure connection using symmetric encryption creates a paradox. The sender and receiver both need the same key for symmetric encryption to work properly — but during that first stage of connection, how do you ensure the connection is secure via symmetric encryption?
If everyone already has the same key, encryption doesn’t matter. This is why there are public and private keys. These keys act in the exact manner as their names describe — public keys, while unique to each device, are accessible to everyone — in fact, you want everyone to have your public key. That ensures other parties can send you an encrypted message. Private keys are only accessible to the device itself, and are used to decrypt messages after public key verification.
So if you were to begin a TLS connection using symmetric encryption, how would you verify that the message was secure? You’d need a new set of symmetric keys to verify. But how would you know that that set of symmetric keys was secure? You could create another set of symmetric keys to verify it. And thus, you find yourself in the chicken and egg paradox.
The way it really works is this: a connection is established using public keys (sometimes referred to as certificates), which are verified via third-party authorities — this ensures the person’s public key actually belongs to them. Once this “handshake” has occurred, the first message is sent using asymmetric encryption, which makes use of the private keys in order to decrypt the message, ensuring no interception of the message. After this first message and the established secure connection, via some fancy math going on in the background, the devices begin to use symmetric encryption to send messages between each other. This helps to speed up the decrypting process.
Public keys encrypt, private keys decrypt. Asymmetric encryption is used for the first message, and symmetric encryption is used for the following messages. Whenever you connect to a “HTTPS” website, this TLS connection is running in the background, ensuring no one is snooping in on your messages. This connection works the same for your MFP as well.
What this means for your MFP with TLS1.3 is that any device connected to it can communicate without worry of message interception or data changes. Due to a unique set of symmetric keys being generated for each connection between each device, it becomes almost mathematically impossible for any data breach to happen.
When your device sends a file to your MFP for print, it sends two types of data: formatting data, and the actual file for print. Essentially, for every line that is printed on a piece of paper, your device includes a “tag” with formatting options — 12 point font, black ink, 1/2 inch left margin, for example — and then pairs that up with the corresponding line. Without a TLS connection, all of the corresponding data — the information on the page — can be intercepted.
And since MFPs have a hard drive that stores all of the data that has passed through the machine, you want to make sure these connections are 100% secure.
Essentially, TLS1.3 is an update to its predecessor with improved cyphers for extra security. There’s also updates to the “handshake” stage (the first step when certifications are verified using public keys) in order to streamline and speed up the process.
One thing you want to be careful with is this streamlined verification stage — if your MFP utilizes single-user verification rather than third-party verification, it can be a major security risk. Essentially, single-user verification is that specific device saying to your MFP “I am who I say I am.” Third-party verification is a trusted source saying “They are who they say they are.”
If someone is attempting to steal your information, and your MFP uses single-user verification, of course the culprit will say they are the intended party — but there is no way to verify if they truly are. Make sure when you are in the purchasing stage to check if the MFP uses single-user or third-party verification — otherwise, your sensitive data could be open to cyberattack.
Your MFP is essentially (and literally) another device on your network — and just as you wouldn’t trust a site without the “HTTPS” code attached to it, you shouldn’t trust a MFP without TLS.

3 min read
Cobb Technologies has been honored as one of the 2025 Best Places to Work in Virginia by Virginia Business and Best Companies Group. This prestigious...

5 min read
Cobb Technologies is honored to hold the SWaM (Small, Women-owned, and Minority-owned Business) certification, awarded by the Commonwealth of...

5 min read
Every year, thousands of Veterans transition from military service to civilian careers in Virginia, bringing invaluable skills and experiences to...