10 min read
What Microsoft's Scan-to-Email Update Means for Your Workflow
There is a major email security update from Microsoft that will disrupt scan-to-email workflows for many businesses unless action is taken before...
Many small and medium businesses think they’re flying under the radar when it comes to cyberattacks - unfortunately, history shows that they’re wrong. It’s been a couple of years since the first WannaCry attack brought networks across the globe to their knees. The ransomware attack spread like wildfire on Friday, May 12th, 2017, and by the time it was contained three days later, the attack had claimed 300,000 digital victims.

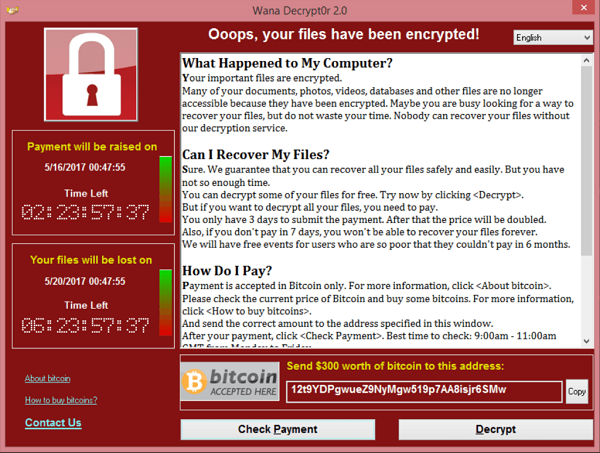
A screenshot of the WannaCry ransom note co. Wikipedia
The ransom fee demanded by the hackers was the equivalent of $300 in bitcoin, with threats of doubling the ransom to $600 as time went on. The fee was relatively low, making it a practical ransom that smaller businesses would be able to quickly pay to get their data back. While most victims did not succumb to negotiating with these cyberterrorists, the hackers still netted themselves $72,500 - which grew to $120,000 by the time they cashed out due to bitcoin fluctuations.
Victims who didn’t pay up were denied access to their systems for three days, their data was kept from them, suspended in a sort of cyber-purgatory. Later reports show that victims who forked over the ransom fee were ignored by the hackers who continued to withhold their data. Although the $300 ransom fee was modest, businesses across the board were disrupted on all levels of the value chain, with losses totaling to around $4 billion.
WannaCry was so universally effective because of its incorporation of EternalBlue. EternalBlue is a cyberattack exploit initially developed by the National Security Agency, and later leaked by the Shadow Brokers hacker group. Since its leak, EternalBlue has been used in various cyberattacks including the NotPetya cyberattack, and the Retefe banking trojan. Shodan, a search engine that indexes devices connected to the internet, estimates (as of August 19th 2019) that there are 950K devices that are vulnerable to attacks EternalBlue. Keep in mind, the figure presented by Shodan only reflects vulnerable devices connected to the internet, it does not take into account the number of non-internet devices that are connected to those devices on a server; the potential future casualties are much higher.
The EternalBlue exploit takes advantage of vulnerabilities in Microsoft’s Server Message Block protocol, a networking protocol that allows users to share and exchange folders, printers and serial ports on a network. SMB is an essential component of networking software that exists in most offices worldwide, making it a worthy target for hackers.
SMB is a networking protocol that allows users to share and exchange folders, printers and serial ports on a network. SMB was designed by Barry Feigenbaum of IBM in 1983, but SMB as we know it is the product of further refinement and additions by Microsoft, Intel, and 3Com. SMB has gone through a few iterations over the past few decades - currently, we are on SMB3, the latest and greatest iteration that provides the most comprehensive security coverage.
SMB 1.0, SMB 2.0, and SMB 3.0 can all simultaneously run on machines on your network. WannaCry exploited weaknesses in SMB 1.0, leading Microsoft to release a patch (MS17-010), but by then it was too late - security experts advised disabling SMB 1.0 on all systems. During the cyberattack, equipment running on SMB 1.0 was affected, causing issues like malfunctioning scan-to-folders and unavailable remote printing options to arise during use.
As businesses grow and change they rely further on technology to provide them with the support they need. The devices we use in our day-to-day lives are constantly evolving, becoming more and more reliant on the internet to provide us with more convenient and reliable services. Unfortunately, this means that they’re becoming more and more susceptible to cyberattacks; anything on a network is fair game for hackers, and the threat just keeps spreading (just check out this recent article about a Canon DSLR that researchers managed to hack). Protecting your livelihood requires you to stay on top of the latest threats so that you can make sure your business can weather the storm.
No business is too small a target when it comes to cyberattacks - take precaution and don’t let the next WannaCry make you cry!
Download out the list below to see how you can better strengthen your business's cybersecurity.
Sources:
“Cyber-attack: Europol says it was unprecedented in scale” - BBC
“WannaCry ransomware bitcoins move from online wallets” - BBC
“Everything you need to know about EternalBlue – the NSA exploit linked to Petya” - Wired
“Decades-Old Network Protocol Puts Companies At Risk And Refuses To Die” - Forbes

10 min read
There is a major email security update from Microsoft that will disrupt scan-to-email workflows for many businesses unless action is taken before...

11 min read
Why should a law firm invest in a strong modern IT strategy? Today’s legal teams depend on secure, reliable technology to protect sensitive...

2 min read
The Louvre’s password became the punchline of a global story after a heist revealed major security concerns for the museum. Reports say the password...