11 min read
Best IT Strategies for Law Firms Going Into 2026
Why should a law firm invest in a strong modern IT strategy? Today’s legal teams depend on secure, reliable technology to protect sensitive...
9 min read
-1.png) Geri Hodnett
Nov 8, 2022 12:49:18 PM
Geri Hodnett
Nov 8, 2022 12:49:18 PM

Your brain is one of the most advanced pattern recognition processors in the universe; we owe our success as a species to the discerning eyes of ancient navigators and the pattern recognition of farmers who used intuition to predict the seasons and weather.
Our brains’ propensity for pattern recognition is so powerful it rules our conscious and subconscious lives; it’s why you see faces in the woodgrain of a door, or struggle to fall asleep as an ear worm plays its way through your head.
So, what do ocean explorers, ancient astronomers, and brain biases have to do with your copier’s security?
Every day, you come to work in your office, and every day, your copier doesn’t fall victim to cyberattack. Until it does.
MFPs, Copiers, Printers, Scanners — all of these devices, despite their functionality, are essentially computers built for a different purpose than a device made for personal use, such as a laptop, desktop, or smartphone. Many offices think of their copier as a printer with the ability to scan and send documents as emails. What it really is, however, is a computer with the added functionality of printing, scanning, copying, and faxing.
Unless you plug a USB into your office copier every time you print a document, your copier is networked — meaning it is connected to the internet, via your office’s server, just like any other laptop, desktop, or smartphone on your network. In the IT and cybersecurity industry, a networked computer is referred to as an endpoint.
Each endpoint connects to the internet through your office’s network, meaning all data that is passed between a computer and the website it is connected to also travels through your server, through digital layers like your firewall and AV software, and hardware layers like your switches, routers, and modems.
Think of the anatomy of a tree: leaves attach to stems, which are connected to twigs, and then branches, then bigger branches, and finally the trunk, which in turn connects to the earth via its roots.
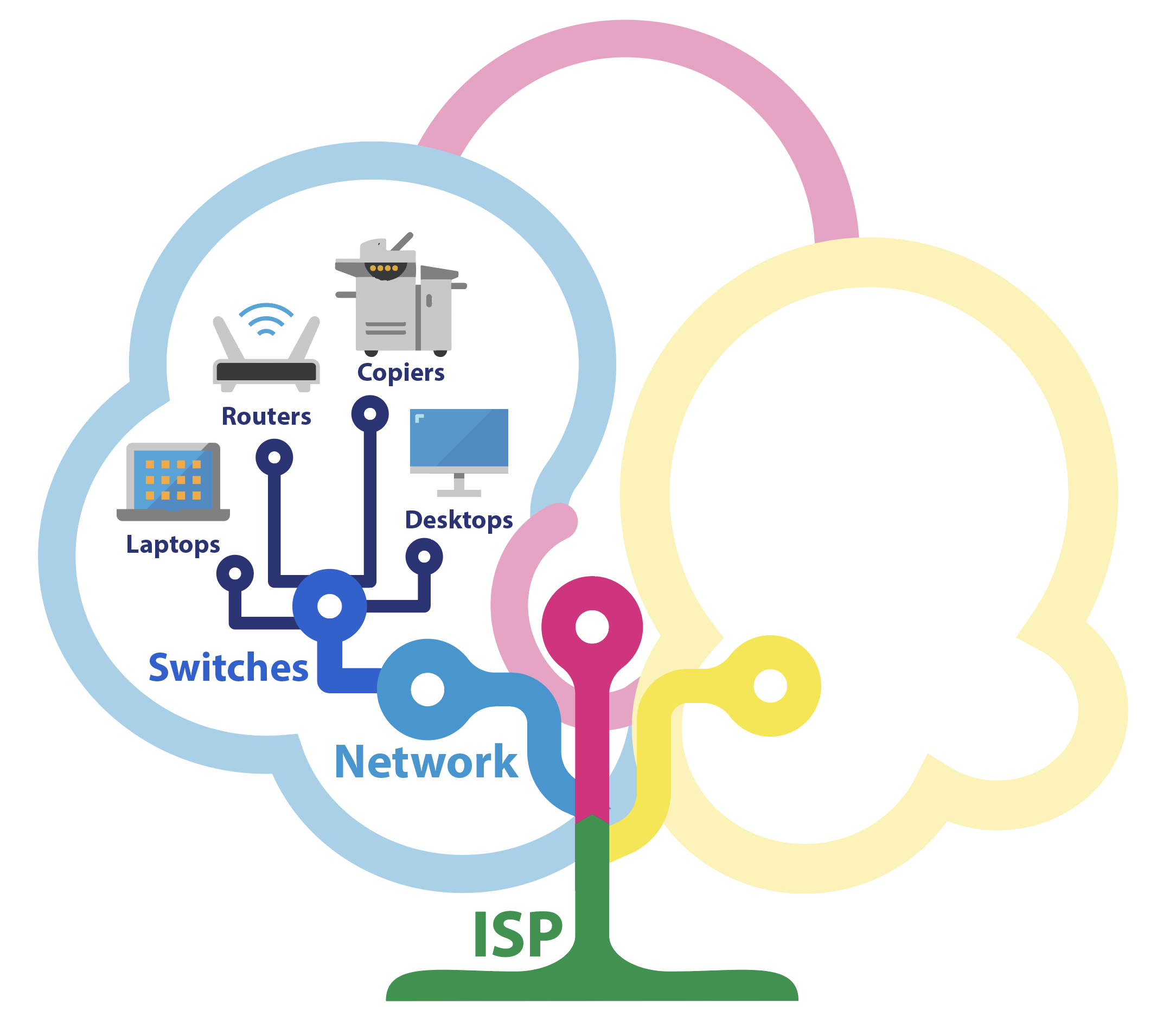
On your office’s network, each endpoint would be an individual leaf on the tree — but even if one leaf is on the opposite side of the tree in relation to another leaf, both leaves are still connected via the complex system of xylem and phloem that transport nutrients throughout the tree.
The same is true for your network: in one way or another, each endpoint on your network shares a connection with every other endpoint.
This is why cybersecurity experts take individual endpoint protection so seriously; and why, if you’ve ever forgotten to use your VPN while connected to airport Wi-Fi, you’ve received a stern talking-to from your system administrator. If your laptop picks up a virus from the airport’s public network, as soon as your laptop connects to your office’s network, the virus will begin to worm its way through your organization, in an attempt to find sensitive data, or network hubs.
A network hub is an endpoint that serves a function that necessitates other endpoints connect to it frequently and in high quantity. And a perfect example of a network hub is, you guessed it, your office’s copier.
*Important disclaimer: Throughout this blog, we will use the term “network hub.” While this term has fallen out of favor compared to the generalized term “endpoint,” for the sake of clarity, we will use “network hub” to describe any endpoint that serves a communal purpose, such as your office copier.
There are two reasons a bad actor would attempt to infiltrate your office’s copier:
When the topic of “copier security” comes up, we mostly tend to think of reason two — but the most likely scenario is number one: other than your routers (and the components of your server itself), the copier is the most used network hub on your server.
Routers, switches, and most other pieces of hardware made to facilitate internet connections (especially business-class hardware), and that serve as network hubs, come with a very high standard of built-in security, are routinely updated, and are continuously monitored for any attempted intrusion or malicious activity passing through it. Your copier, however, can often be a blind spot on your network’s security.
Copiers usually do not come with the same level of built-in security as devices like routers and switches, and AV and firewall software are not always designed with printers in mind, nor come pre-installed.
Even when the time comes for you to part ways with your copier, you still need to consider the security risk the copier poses. As mentioned above, the hard drive of your copier stores the information of printed, scanned, and copied documents that pass through it. Therefore, if your copier is shipped to a warehouse or landfill, anyone with access to those facilities will also have access to all of the data stored on your copier’s hard drive. Because of this, when the end of your copier’s life comes to pass, it’s always a good idea to delete all of the information on your copier’s hard drive, and then physically destroy the hard drive, as even deleted data can be pulled from the physical components of a hard drive.
If you have cyber liability insurance, you may be asked to show a certificate of destruction for your copier’s hard drive. Your copier service provider should be able to conduct the destruction and provide you with the corresponding certificate. Even if you don’t have cyber liability insurance, it’s always a good idea to obtain a certificate of destruction.
So how exactly does a bad actor use an unsecured copier to infiltrate your network?
Imagine a scenario where an unsecured copier is discovered by a bad actor from outside your organization. The rest of your network is locked up tight: your firewalls and AV/EDR software protect and monitor your devices for any suspicious activity.
However, your office’s copier offers what cyber security experts refer to as an attack surface: an endpoint on a network that a bad actor can use to find weaknesses within your organization’s network.
From this attack surface, the bad actor can begin to move laterally throughout your network by finding the endpoints the copier is connected to, the applications that are embedded on your copier, and access any contact information like email names and passwords that are stored on your copier.
For example, a copier connected to a phone line can give a bad actor the opportunity to “dial in” to the copier by sending it a fax, which is then used to gain shell access to the OS running on the copier. From here, the bad actor can use credentials they find on the compromised copier to attempt to attack other devices on your network.
Unfortunately, there’s many different avenues available to bad actors to infect devices with malware, ransomware, and other viruses, and they needn’t scour public wi-fi networks for targets. The most common form of intrusion takes place via phishing.
To make matters worse, the average cyber attack costs small businesses $200K.
There are three consequences your organization will face if an intrusion attempt is successful, like a ransomware attack:
For ease of reading, the following examples will focus on the consequences of a ransomware attack, as they are the most damaging form of intrusion, and other than small cons involving untraceable e-gift cards, are the most common cyber attack.
If your network is infected with ransomware, your organization will usually be completely locked out of your files, and any systems that connect to your network. Ransomware infects networks slowly to dodge the watchful eye of your AV or EDR software, and snoops around for accounts on your network with a high-level of access to critical systems. Once it has infected your administrative accounts, ransomware encrypts your files and access to your systems, leaving the bad actors with sole access to the encryption key.
The bad actors will then demand a ransom be paid by your organization to once again access your files, usually paid in the form of bitcoin or another cryptocurrency. However, even paying your ransom isn’t guaranteed to grant you access to your network and files — the bad actors hold all the cards, and have been known to continue to demand additional payments.
Other than the cost of the ransom you’ll need to pay to access your network, you’ll also be responsible for any damages your employees or clients face. Cyber liability insurance can help pay these costs, but if your insurer finds any breach in your insurance clauses, you can be found responsible for 100% of the bill.
NIST guidelines state that any organization that experiences a breach must report the breach to any affected client or employee, as well as the federal government. In order to make sure your organization follows all of the government’s guidelines, and properly reports the breach, it is highly recommended to partner with a lawyer who can help you through the process. While the mandatory reporting is necessary to protect any affected party, it is usually seen as a blemish on your brand’s reputation by your clients, and 60% of business that suffer a cyber attack go bankrupt after six months as a consequence of the operational, monetary, and legal challenges that follow.
Canon, the authority on copier security, recommends to improve your copier’s security by doing the following:
In a medium sized office, the average copier is used by 15 to 20 different employees, often from different departments, and is often located in an open area for ease of access and use.
By controlling access to your copier, you can reduce the opportunity for information to be stolen from your copier. The most effective method for controlling access to your copier is by installing print management software. Print management can secure your printing, copying, and scanning operations by offering the following features and benefits:
Copiers don’t just store contact data — they hold onto the actual image of the documents they print, copy, and scan, and if they are integrated with any software or server functionality, they will also have direct lines of access to those applications.
If you want to make sure all of these data points and connections secure, your copier should have the ability to do the following:
As detailed above, as a network hub, your copier is the perfect target from which to stage a cyber attack. To properly defend against such an intrusion, your copier should have the ability to:
Print management software can be used for more than controlling who accesses your copier — it can be used manage your copiers, your print drivers, and any other infrastructure your organization uses for your printing, scanning, and faxing operations. This helps take the burden of managing your copiers off of your IT team, and allows them to focus more on your network’s security. To properly manage and monitor your printers, your copier should have the ability to do the following:
There is no such thing as a 100% secure network. If your organization does fall victim to a cyber attack, following regulations and guidelines set out by the federal government can make your recovery quicker, and your costs lessened. To properly address regulations, your copier should have the ability to:
A secure copier means a happy IT team: when they spend less time managing, monitoring, and interacting with your copier, they can spend more time protecting the rest of your network. Threats are not sparse — it is estimated that a company experiences a breach every 39 seconds, and more than 60% of organizations across the world have experienced some form of cyber attack. With so many threats facing your office’s network, every second your IT team can spend protecting it is another potential breach thwarted.
This is why it’s important to not only consider the security-based features of your copier, but it’s reliability as well. To learn more about Canon copiers’ reliability, view Canon’s white paper.
If you’d like to improve the security of your copier, there’s never been a better time to do so, as now, Canon copiers come with the ability to make use of Golden Master AV software, which provides the most advanced anti-virus security available on the market today, via EDR technology.

11 min read
Why should a law firm invest in a strong modern IT strategy? Today’s legal teams depend on secure, reliable technology to protect sensitive...

2 min read
The Louvre’s password became the punchline of a global story after a heist revealed major security concerns for the museum. Reports say the password...

6 min read
Organizations of all sizes handle enormous volumes of data. Data is one of the most valuable assets of any organization.Unfortunately, it’s also a...